Remote Monitoring & Management
The N-able RMM gives you a comprehensive set of tools to efficiently secure, maintain, and improve IT in a single dashboard. Having all the tools you need to run your IT systems in one place makes it easier to manage and save money at the same time. Remotely monitor desktops, laptops, servers, mobile devices across operating systems and platforms. Features included in N-able RMM are:
Network Path Visualization
Remote Access
Automated Monitoring and Maintenance
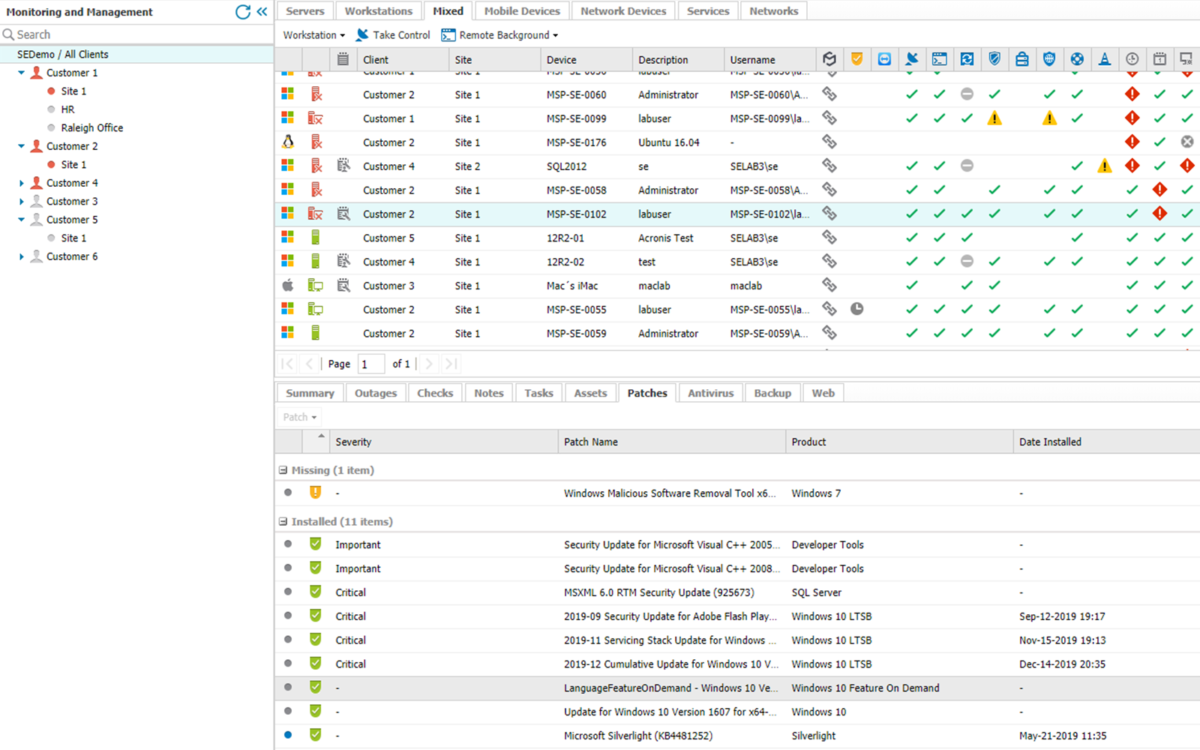
Patch Management
Prescriptive Data Analytics
Data-Breach Risk Intelligence
Managed Antivirus
Web Protection
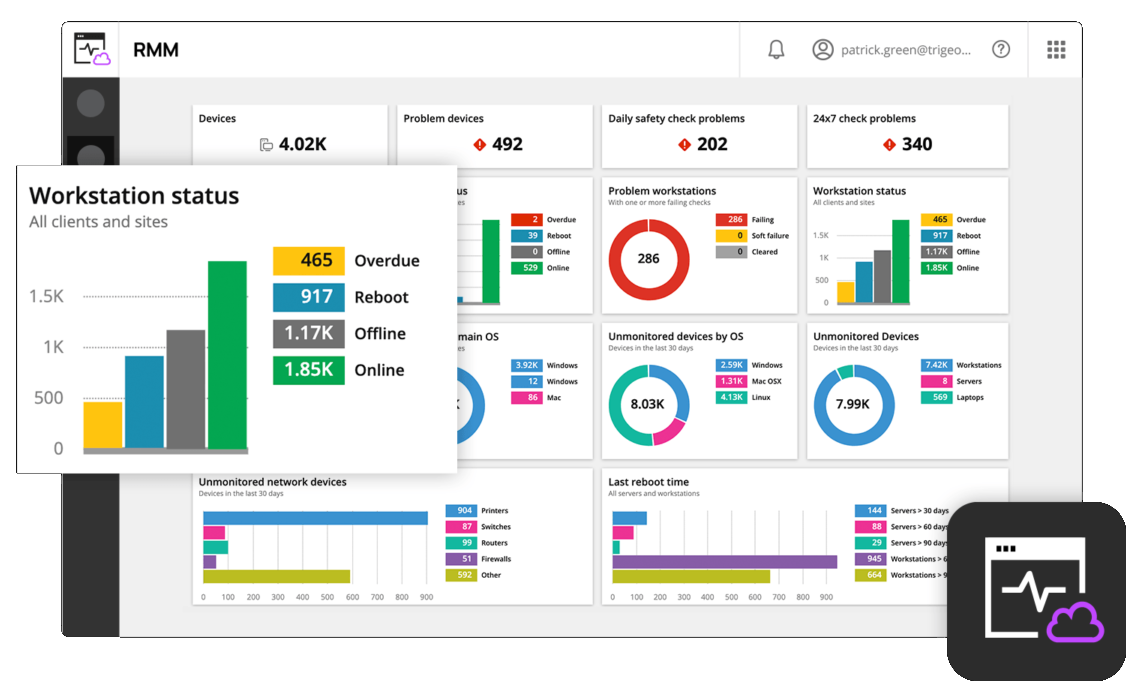
Keep Your Environment Healthy
Alerts:
Get notifications about device availability, performance, security, and backup statuses.
Performance checks:
Easily health-check hardware and software on workstations, servers, and network devices across multiple work locations.
Security monitoring:
Monitor antivirus scanning statuses, errors in event logs, and much more.
Monitor Everything
Windows, Mac, and Linux compatibility:
Unlike other remote monitoring software that focuses on a single platform, N-able Remote Monitoring & Management enables you to keep track of workstations and servers across platforms and operating systems including Windows, OS X, and multiple versions of Linux.
Network performance monitoring:
Discover, import, and monitor critical network devices using SNMP, such as firewalls, routers, printers, and switches.
Mobile device monitoring:
Keep track of smartphones and tablets with mobile device checks and monitoring.
Virtual machine monitoring:
Run checks on all virtual sessions and virtual machines under your control.
Proactive Maintenance
Background maintenance:
Fix issues without disrupting end users or causing downtime by using remote command lines and custom scripts, and by managing system processes and services.
Maintenance windows:
Set scheduled maintenance to run during off hours so you don’t disrupt employees’ productivity or raise false downtime alarms.
Granular roles and permissions:
Set strong rules around who can and cannot access data and systems based on their position within the organization.
Automation and bulk actions:
Standardize your checks, rules, and tasks across sites, servers, and workstations. And take full advantage of our automation and scripting tools to help you perform bulk actions automatically across networks and work sites.
