In the previous chapter of our ‘Security focused MSP’ blog series, we explained what the Layered Security Approach is. We explained how MPmail / MPmail Avanan helps protect against threats in the Internet layer, through Mail Filtering.
A reminder for what the different layers are in the Layered Security Approach:
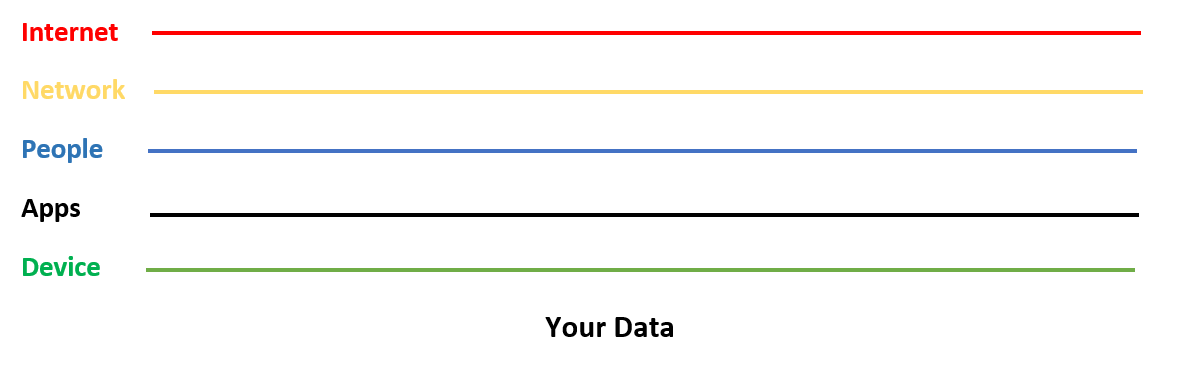
You can use this approach to explain to your customers:
- What each layer is.
- How an attack can touch each/all the layers.
- What you can provide to stop threats at each layer.
Threats today are considerably more complex than they were a few years ago. Hence the need to increase the number of layers that need protection, as well as their level of security.
In this next chapter, we will continue with the Internet layer and discuss another aspect of protection – Web Filtering.
Web Filtering is often referred to as content or internet filtering. It’s a piece of software that can control or restrict what pages or content a user is able to access on the internet, usually through a block and allow list. It can be used by a school to its students, by a library to its visitors, or by a parent to a child’s computer.
Below are a few common ways web filtering is deployed:
- Client-side filter – an agent that is installed on an endpoint.
- ISP filter – implemented at the provider level.
- Network-based filter – such as a web proxy.
- DNS-based filter – implemented by the DNS server.
When a content filter is bought into discussion, most people will have a negative sentiment as filters are usually associated with censorship. On the contrary though, web filters can be incredibly effective in protecting users from phishing and malicious websites – as it blocks them from reaching these sites at all.
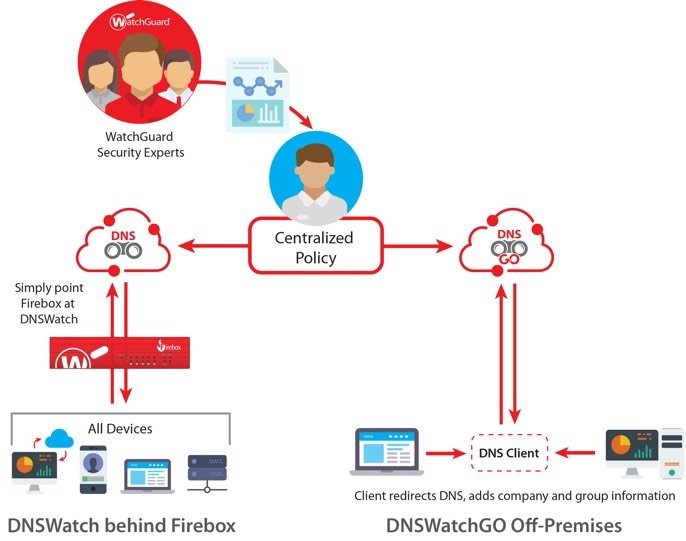
This is what can be achieved with WatchGuard’s DNSWatch. DNSWatch is a cloud-managed platform that is deployed on a network that a Firebox UTM appliance is protecting, or as an endpoint agent called DNSWatchGO. DNSWatchGO allows you to enforce filtering policies to remote/mobile workers, to ensure they receive the same amount of protection as their office-based counterparts. These policies could consist of websites that are allowed or blocked based on their content, such as adult material, social media, or classed as a security threat. These content-based categories group domains or websites together, are managed by WatchGuard in conjunction with other DNS filtering vendors. This ensures the list of websites from each category is continuously updated from multiple sources. These websites can also be configured to be allowed or blocked at certain times of the day.
The blocked-page a user sees when they try accessing a blocked website can be customised and white-labelled, so it’s not just a generic page. If a user comes across a phishing site, the blocked page will also advise them of the malicious threat and give them a quick video on how to spot phishing attempts in the future. This allows your clients to see the added value you are providing, as their security-focused provider.
Finally, another powerful feature of DNSWatch is the ability to protect a network, just by pointing it to the external IP address of another network. This essentially hijacks and reroutes all DNS traffic to be checked by DNSWatch, allowing you to enforce your policies and protect users regardless of what network equipment they are running.
DNSWatchGO can be purchased standalone or as part of the Passport bundle. This also includes AuthPoint MFA and Panda Adaptive Defense 360. (Note this will be renamed to WatchGuard Endpoint Protection, Detection & Response EPDR later in the year).
Reach out to us at watchguard@sofsol.co.nz if you’d like to see DNSWatchGO in action. You can also get the Passport (NFR) bundle for free internal use until September 30th, 2021.
